TLDR;
The new Eldorado ransomware targets Windows and VMware ESXi systems, with sixteen victims primarily in the United States across various industries. Groupe-IB researchers observed Eldorado’s activities and announced the threat on RAMP forums. This ransomware uses the ChaCha20 algorithm for encryption and generates unique keys for each locked file. It deletes shadow volume copies to prevent file recovery and deletes itself to avoid detection. Experts’ recommendations include multi-factor authentication, EDR solutions, regular backups, AI-based analytics, and employee awareness. It is not recommended to pay the ransom.
Eldorado, a customizable ransomware that attacks Windows and Linux systems
Eldorado has recently emerged in the ransomware-as-a-service (RaaS) space. RaaS is a model in which ransomware developers rent or sell their malware to other cybercriminals. This allows individuals without advanced technical skills to launch attacks by encrypting your data and returning it to you in exchange for a ransom.
According to cybersecurity researchers at Group-IB, Eldorado is not a reinvention of a previous threat actor but an entirely new entity. Its activities probably started in March this year which was observed by the start of its advertisements on the dark web to recruit competent affiliates.
Eldorado’s encryption tool was designed to work on Windows and Linux devices. Since March, it has claimed sixteen victims, mostly in the real estate, education, healthcare, and manufacturing sectors. Its developers claim not to rely on previously published sources and offer unique customization options for their affiliates.
The malware uses the ChaCha20 algorithm for encryption and generates a unique 32-byte key and 12-byte nonce for each of the locked files. The keys and nonces are then encrypted using RSA with the Optimal Asymmetric Encryption Padding (OAEP) scheme.
After the encryption stage, files are appended the “.00000001” extension and ransom notes named “HOW_RETURN_YOUR_DATA.TXT” are dropped in the Documents and Desktop folders.
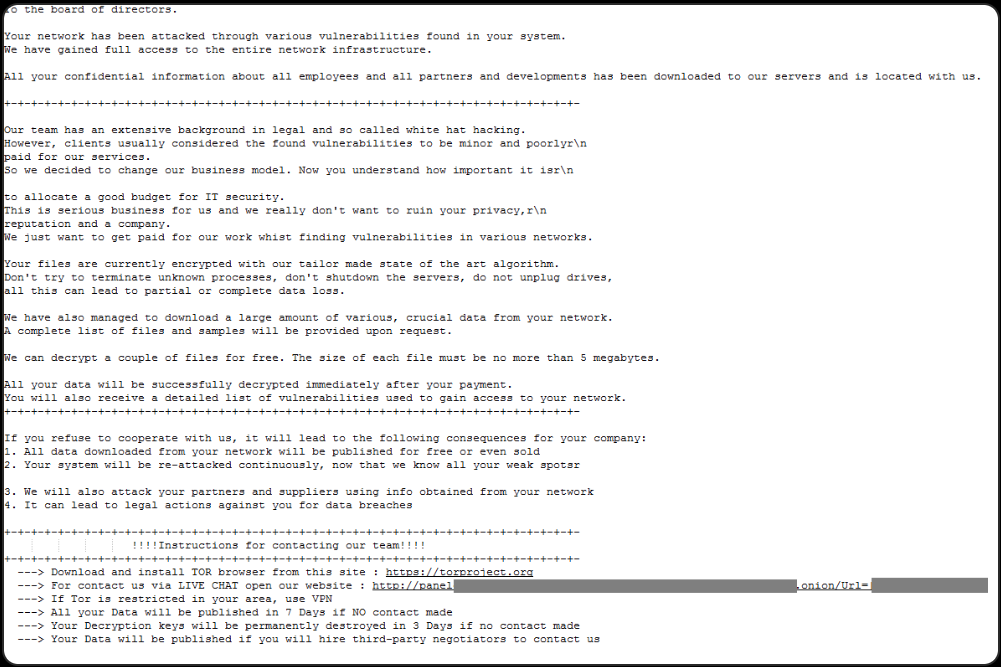
Image: The Eldorado ransom note
Source: Group-IB
For example, under Linux, it is possible to choose the directories to encrypt. On Windows, users can choose directories, avoid local files, target network shares to specific subnets, and prevent malware from self-destructing.
By default, Eldorado ransomware is set to self-remove to prevent security teams from analyzing it. Although the group claims to have a data leak site, it is currently offline.
Ransomware attacks have become one of the most devastating means of cyberattack in recent years
The number of companies whose data has been fully encrypted as a result of these attacks is constantly increasing. Many attacks are specific to an organization and have a potentially huge impact. Hacker groups take their time before starting the data encryption process. Their goal is to first infect online backups and as many devices connected to the network as possible. This upstream work can sometimes take several months. Once the ransomware is executed, it can encrypt most data or even all files.
In the event of such a catastrophic event, there are few actions possible, especially if the backups have been affected or are no longer up to date. The number of companies that have had to cease operations after their data was encrypted is incredibly high.
How can I protect against ransomware?
To protect against ransomware, you can follow several simple security measures:
- 1. Activate multi-factor authentication
- 2. Have a back-up strategy, firewalls, and anti-virus solutions
- 3. Endpoint detection and response (EDR)
- 4. Run employee cybersecurity training
- 5. Keep your systems and software up to date
- 6. Conduct a ransomware penetration test, plan regular audits and risk assessments